Template Information
Widget by :MIXGADGTES Soft
Thursday 18 July 2013
Tuesday 2 July 2013
What Is Keylogger And How To Be Safe From Keyloggers?
 In this tutorial i am going to talk about the most use piece of software besides from RAT by hackers to observe your activities on your computer and that is keyloggers. A keylogger is a software or hardware device which monitors each and every key typed by you on your keyboard. I am going to talk about different types of key-logger and how to be safe from key loggers. So lets learn something about key loggers.
In this tutorial i am going to talk about the most use piece of software besides from RAT by hackers to observe your activities on your computer and that is keyloggers. A keylogger is a software or hardware device which monitors each and every key typed by you on your keyboard. I am going to talk about different types of key-logger and how to be safe from key loggers. So lets learn something about key loggers.______________________________________________
1. What is keylogger ?
______________________________________________
You might have heard about keyloggers but really dont know what they are reading this article will clear your mind. A keylogger also know as keystroke logger is software or hardware device which monitors each and every key typed by you on your keyboard. You can not identify the presence of keylogger on your computer since it runs in background and also it is not listed in task manager or control panel. It can be used by parents to keep eye on their childrens or company owner to spy on their employes.
______________________________________________
2. How it can harm you ?
______________________________________________
In this section i will talk about how keylogger can harm you in different ways for example It can be used by your enemy or friend to get sensitive information such as your username and password, Bank credit card details, or any other activities you do on your computer.
Example: You login in to your Facebook account from a computer in which keylogger is install then your username and password will be captured.
______________________________________________
3. Types of keyloggers
______________________________________________
There are two types of keylogger hardware keylogger and software keylogger. Software keylogger is install in your computer where as a Hardware keylogger is attached to your keyboard. Looking at below images will clear your mind.
HARDWARE KEYLOGGER
SOFTWARE KEYLOGGER
______________________________________________
4. How to Protect yourself from keyloggers ?
_____________________________________________
Keylogger can be used by your enemy to get sensitive information such as your Bank credit card details, or password of any social networking sites etc. In order to be safe keep following points in your mind.
Never use your online banking from cyber cafe. If you want to use then you can try this method. open notepad and type anything Then copy and paste each word that comes in your username or password.
You can even use above method to protect your Facebook profile, yahoo or gmail id.
When you enter cyber cafe make sure that no hardware device is attached to keyboard wire. Its look something similar to above image.
Introduction To Basic Terminal Commands For Linux
In this tutorial you will learn to use Linux terminal. You will learn to navigate on the terminal, learn to create and remove file and much more. Most of this commands also works on Mac Os X and power shell on windows.
______________________________________________________
What Is Terminal ?
______________________________________________________
Basically you are reading this tutorial because you are new to linux or want to learn using terminal to navigate. Before you get started you must have linux installed or running virtually on your computer. I would recommend downloading fedora or ubuntu (If you have trouble installing ubuntu leave a comment below and i will post a tutorial).
_____________________________________________________
Commands To Remember
______________________________________________________
This are some of commands you must remember which will help you to use terminal more easily.
ls - it will list all files and folder in your current directory
ls -l it will give detailt listing of all files and folders
ls -a it will list all files and folder in your current directory including hidden files (files and folders that begin with period)
pwd will print your working directory or simply your current directory
______________________________________________________
Navigating In Terminal
______________________________________________________
Here i may refer folder as directory so dont get confused. This is the term we use in linux for folders.
cd - cd stands for change directory. we use cd follow by path address to navigate ro that folder.
Eg: cd Desktop will make desktop as my current directory.
cd / will make root as you current directory
cd ~ will make home as your current directory
Typing cd alone is same as cd ~ and it will make home as your current directory
cd .. will make parent directory i.e directory above your current directory
cd ../../ will take you two folder up
______________________________________________________
Creating Files And Folder
______________________________________________________
mkdir - we use mkdir follow by path or folder name to create a directory
Eg mkdir car will create directory car in your current directory
to create folder recursively i.e folder inside folder inside folder we use -p flag
Eg mkdir -p vehicles/car/truck will create directory vehicles in your current directory which have car inside it and car has directory truck in it.
touch - we use touch follow by file name to create empty file.
______________________________________________________
Removing Files And Folders
______________________________________________________
rmdir - we use rmdir follow by path to to remove any directory. This will not work if folder you are trying to remove has something in it.
rm -r to remove file recursively which can not be removed by rmdir
rm - We use this command to remove files
How To Block Youtube Ads ?
Most of you get bored or annoyed due ads playing before youtube videos. Today i will share with you an amazing peace of programme called Block YouTube Ads . It removes all video ads before and during videos, as well as removes all those ads that pop at the bottom of the screen while the video is playing. It works on all major browser such Internet explorer, google chrome and mozilla firefox.
How to do ?
1. Download Youtube Ads Blocker
2. Double click on downloaded file.
3. Follow the on screen instruction.
Friday 14 June 2013
Beginning Red Hat Linux 9 Ebook
Author: Sandip Bhattacharya, Mark Mamone , Kapil Sharma, Deepak Thomas, Simon Whiting, Shishir Gundavaram, Pancrazio De Mauro.
Red
Hat Linux 9 is a powerful, flexible open source operating system. Its
popularity is growing, both in home use and in corporate environments of
all sizes. Its user interface makes it every bit as accessible as other
operating systems, and its open source pedigree opens the doors to a
mind-blowing amount of free software.
Red Hat has become associated to a large extent with its enterprise operating system Red Hat Enterprise Linux and with the acquisition of open-source enterprise middleware vendor JBoss.
Red Hat provides operating system platforms, middleware, applications,
management products, and support, training, and consulting services.
Red Hat creates, maintains, and contributes to many free software projects and has also acquired several proprietary software packages and released their source code under mostly GNU GPL while holding copyright under single commercial entity and selling user subscriptions. As of April 2012, Red Hat is the largest corporate contributor to the Linux kernel.
Red Hat, Inc created its subsidiary Red Hat India to deliver Red Hat software, support, and services to customers in India.[Colin Tenwick, vice president and general manager of Red Hat EMEA said that "the opening of [Red Hat India] is in response to the rapid adoption of Red Hat Linux in the subcontinent... Demand for open source solutions from the Indian markets is rising and Red Hat wants to play a major role in this region." Red Hat India has worked with local companies to enable adoption of open source technology in both government[and education.
In 2006 Red Hat India had a distribution network of more than 70 channel partners spanning 27 cities across India. Red Hat India's channel partners included Ashtech Infotech Pvt Ltd, Efensys Technologies, Embee Software, Allied Digital Services, and Softcell Technologies. Distributors included Integra Microsystems, Ingram Micro, GT Enterprises, and Sonata Software.
Red Hat creates, maintains, and contributes to many free software projects and has also acquired several proprietary software packages and released their source code under mostly GNU GPL while holding copyright under single commercial entity and selling user subscriptions. As of April 2012, Red Hat is the largest corporate contributor to the Linux kernel.
Red Hat, Inc created its subsidiary Red Hat India to deliver Red Hat software, support, and services to customers in India.[Colin Tenwick, vice president and general manager of Red Hat EMEA said that "the opening of [Red Hat India] is in response to the rapid adoption of Red Hat Linux in the subcontinent... Demand for open source solutions from the Indian markets is rising and Red Hat wants to play a major role in this region." Red Hat India has worked with local companies to enable adoption of open source technology in both government[and education.
In 2006 Red Hat India had a distribution network of more than 70 channel partners spanning 27 cities across India. Red Hat India's channel partners included Ashtech Infotech Pvt Ltd, Efensys Technologies, Embee Software, Allied Digital Services, and Softcell Technologies. Distributors included Integra Microsystems, Ingram Micro, GT Enterprises, and Sonata Software.

Labels:
Ebooks
,
MORE STUFFS
Wednesday 5 June 2013
How to Format your Linux or any debian file system install pen drive or Sd cards
we all are using linux and their other distributions but some time when we install it in pen drives or sdcards then it is very
chunky and difficult to format it with the windows with out any third party software.
So, here is a solution just download this software and format any pendive or sdcards installed Linux filesystem and use it as your normal pen drive.
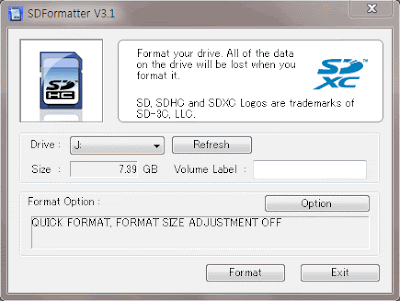
SD Formatter 3.1 for SD/SDHC/SDXC
This software formats all SD memory cards, SDHC memory cards and SDXC memory cards. SD Formatter provides quick and easy access to the full capabilities of your SD, SDHC and SDXC memory cards.
The SD Formatter was created specifically for memory cards using the SD/SDHC/SDXC standards. It is strongly recommended to use the SD Formatter instead of formatting utilities provided with operating systems that format various types of storage media. Using generic formatting utilities may result in less than optimal performance for your memory cards.
The SD/SDHC/SDXC memory cards have a "Protected Area" on the card for the SD standard's security function. The SD Formatter does not format the "Protected Area". Please use appropriate application software or SD-compatible device that provides SD security function to format the "Protected Area" in the memory card
Labels:
PC software
,
TRICKS
Tuesday 28 May 2013
How to use Flash Professional CS5 - Adobe :Download it in PDF from here adsolutly free.
What is Adobe Flash CS5?
Adobe Flash CS5 is a popular multimedia development platform used to add interactivity and animation to web pages. Web developers, animators, and application developers love Adobe Flash CS5 because they are able to create beautiful animations, graphics, advertisements, and various web page additions through Flash CS5.
Adobe Flash (formerly called "Macromedia Flash") is a multimedia and software platform used for authoring of vector graphics, animation, games and Rich Internet Applications (RIAs) which can be viewed, played and executed in Adobe Flash Player. Flash is frequently used to add streamed video or audio players, advertisement and interactive multimedia content to web pages, although usage of Flash on websites is declining.
Flash manipulates vector and raster graphics to provide animation of text, drawings, and still images. It allows bidirectional streaming of audio and video, and it can capture user input via mouse, keyboard, microphone and camera. Flash applications and animations can be programmed using the object-oriented language called ActionScript. Adobe Flash Professional is the most popular and user-friendly authoring tool for creating the Flash content, which also allows automation via the JavaScript Flash language (JSFL).
Adobe Flash CS5 is a popular multimedia development platform used to add interactivity and animation to web pages. Web developers, animators, and application developers love Adobe Flash CS5 because they are able to create beautiful animations, graphics, advertisements, and various web page additions through Flash CS5.
Adobe Flash (formerly called "Macromedia Flash") is a multimedia and software platform used for authoring of vector graphics, animation, games and Rich Internet Applications (RIAs) which can be viewed, played and executed in Adobe Flash Player. Flash is frequently used to add streamed video or audio players, advertisement and interactive multimedia content to web pages, although usage of Flash on websites is declining.
Flash manipulates vector and raster graphics to provide animation of text, drawings, and still images. It allows bidirectional streaming of audio and video, and it can capture user input via mouse, keyboard, microphone and camera. Flash applications and animations can be programmed using the object-oriented language called ActionScript. Adobe Flash Professional is the most popular and user-friendly authoring tool for creating the Flash content, which also allows automation via the JavaScript Flash language (JSFL).
Labels:
MORE STUFFS
Subscribe to:
Posts
(
Atom
)
©2012
MIX GADGETS Beta
is powered by
Blogger
-
Template designed by
Designed and powered by Mix Gadgets.